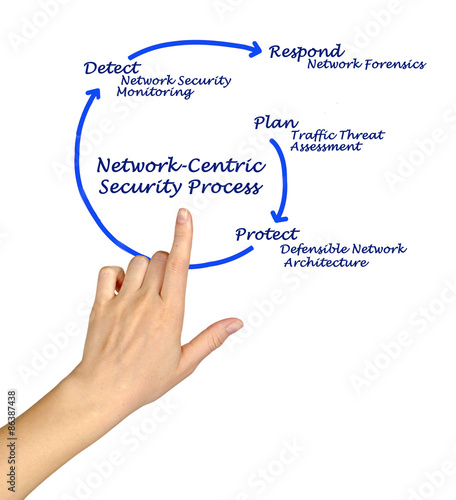
Diagram of network-centric security process
Keywords
network,
security,
process,
protection,
defense,
defensible,
cyberspace,
architecture,
detection,
secure,
monitoring,
forensic,
planning,
plan,
traffic,
threat,
assessment,
information technology,
information,
technology,
diagram,
concept,
safety,
safe,
attack,
hack,
hacker,
virus,
software,
program,
development,
developer,
man,
male,
person,
hand,
vertical,
lecture,
lecturer,
expert,
presentation,
finger,
pointing,
virtual,
screen